1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
| #include <stdio.h>
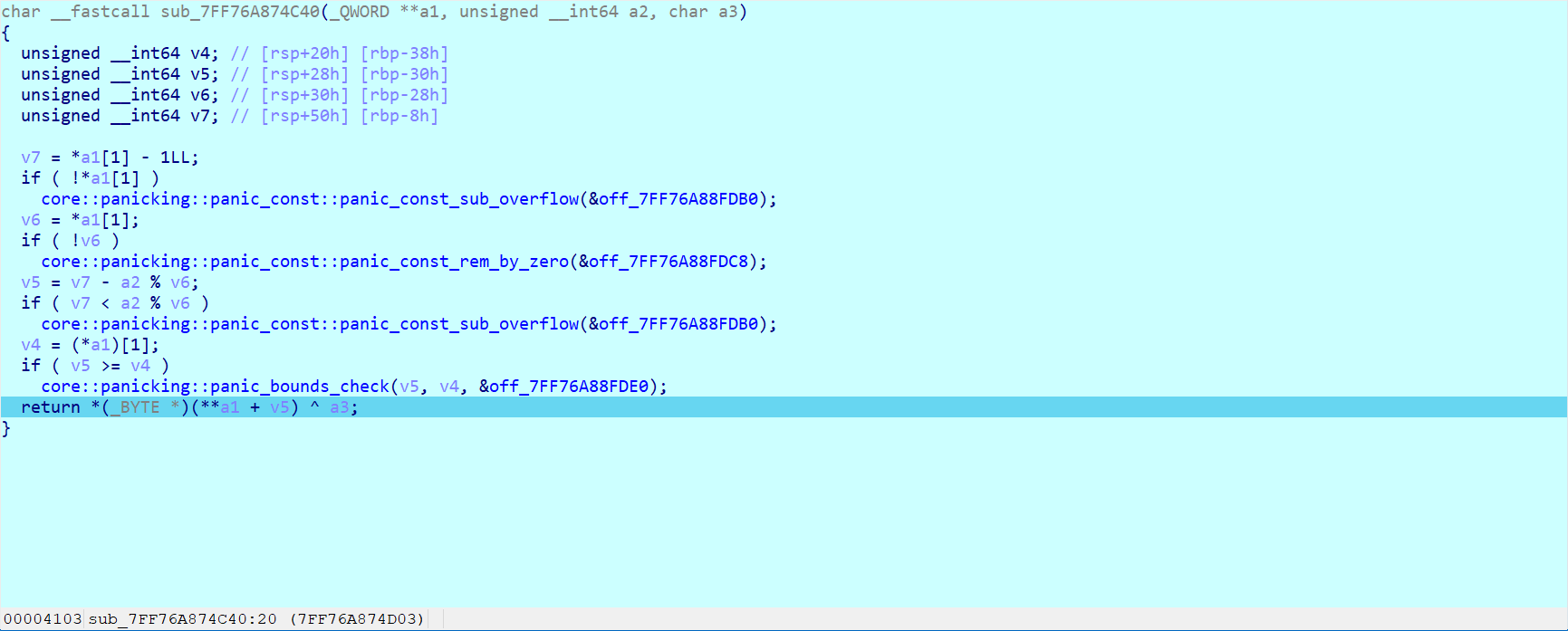
void dealboxdec(unsigned char* Src, unsigned char* box, int len) {
unsigned _int16 v11;
for (int k = 0; k < len; k += 4) {
v11 = Src[k + 3];
Src[k + 3] = (Src[k + 3] << 3) | (Src[k + 0] >> 5);
Src[k + 0] = (Src[k + 0] << 3) | (Src[k + 1] >> 5);
Src[k + 1] = (Src[k + 1] << 3) | (Src[k + 2] >> 5);
Src[k + 2] = (Src[k + 2] << 3) | (v11 >> 5);
}
for (int j = 0; j < 44; ++j) {
for (int i = 0; i < 256; i++) {
if (box[i] == Src[j]) {
Src[j] = i;
break;
}
}
}
}
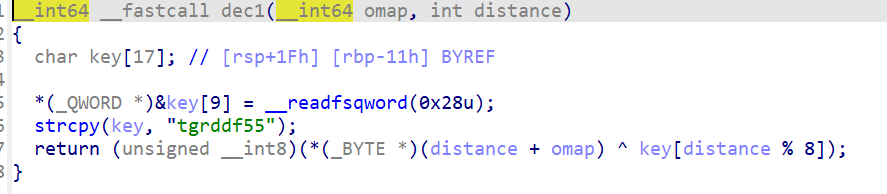
void dec1(char *key,unsigned char *box, unsigned char *Src) {
int i = 0;
do
{
box[i] = i;
++i;
} while (i < 256);
}
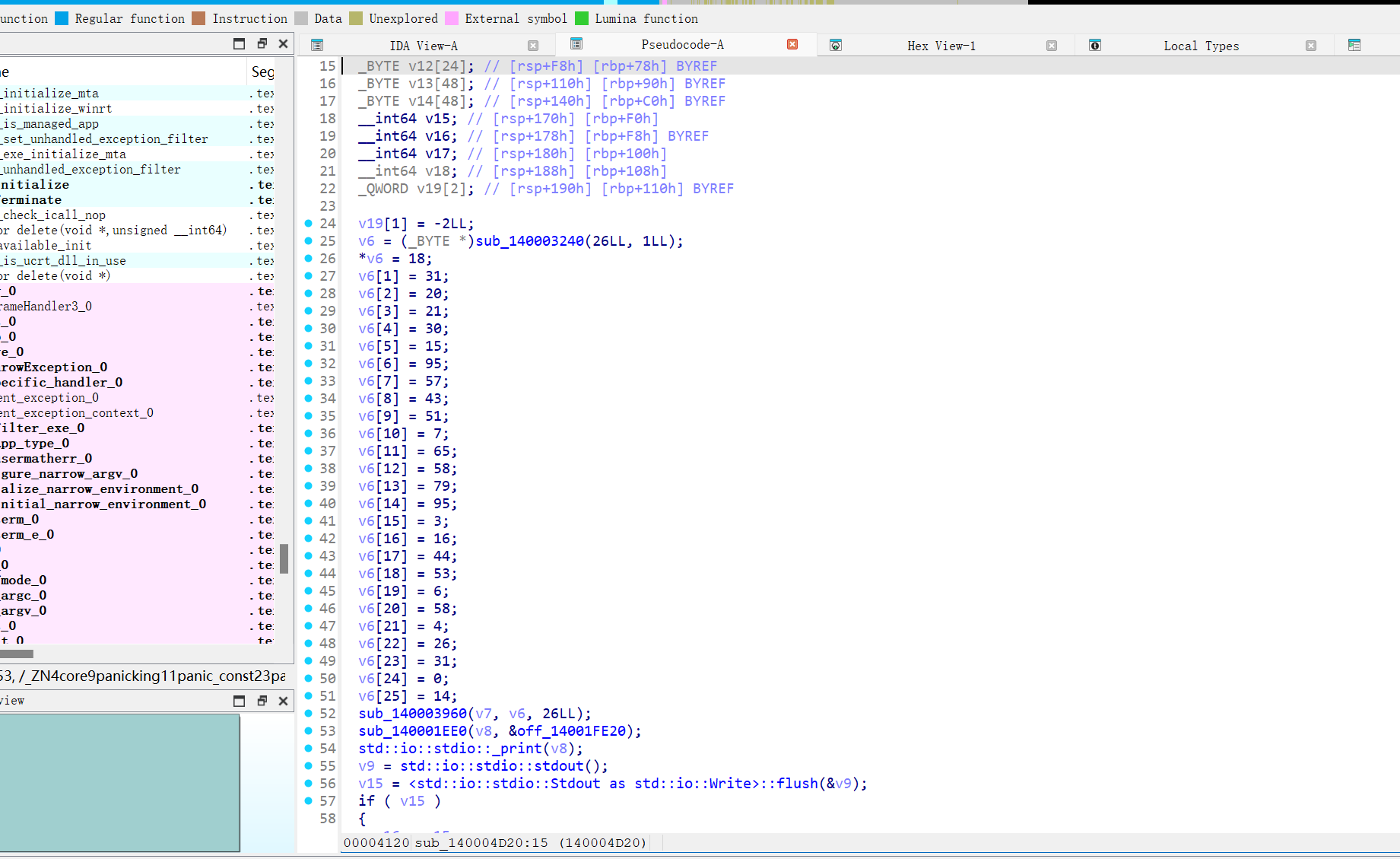
void dec2(unsigned char* box) {
int v21,v22,v17,v18,v16;
char* v23;
unsigned __int64 result;
unsigned char v31[256] = {
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49, 0x65, 0x61, 0x73, 0x79, 0x5F, 0x47, 0x55, 0x49,
};
v21 = 0;
v16 = 256;
v17 = 0;
do
{
v22 = *((unsigned __int8*)box + v21);
v17 = (v22 + v31[v21] + v17) % 256;
v23 = (char*)box + v17;
result = (unsigned __int8)*v23;
box[v21++] = result;
*v23 = v22;
--v16;
} while (v16);
}
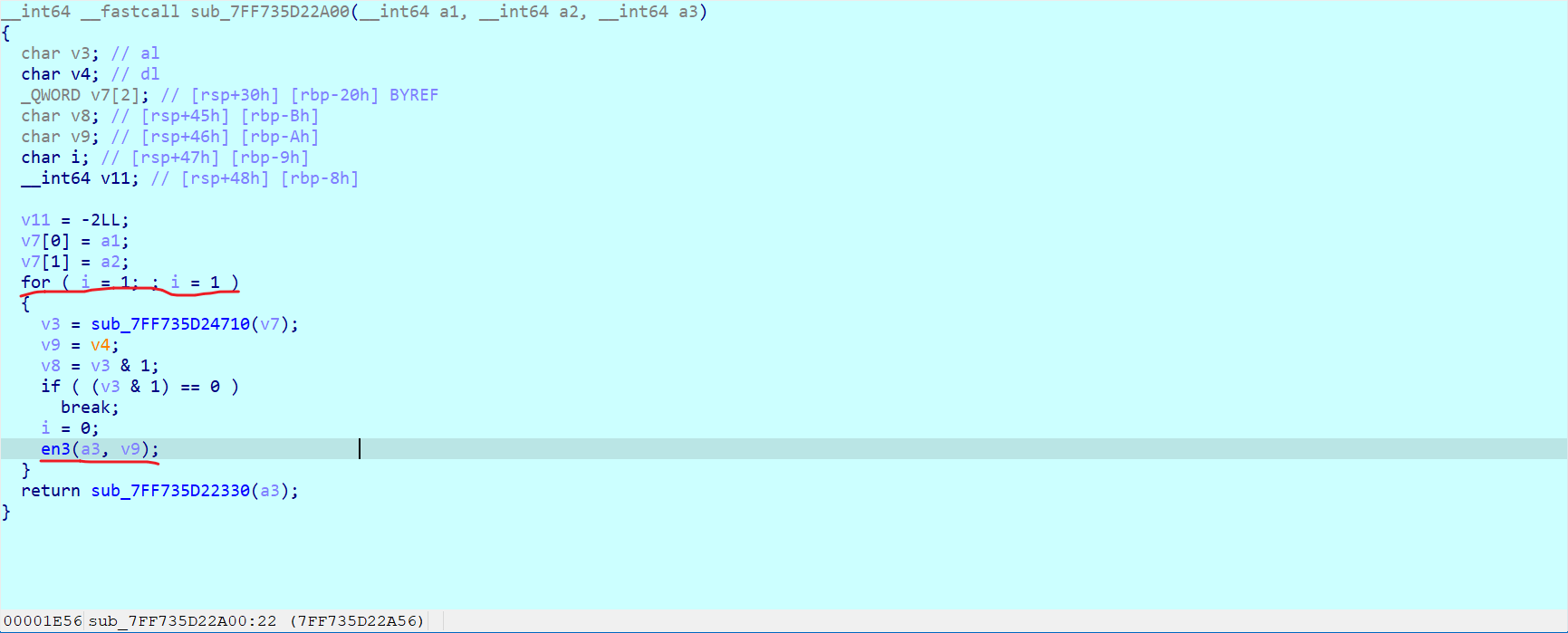
void dec3(unsigned char* box,unsigned char* Src) {
int v25,v6,v27;
v25 = 0;
int len = 44;
v6 = 0;
for (int m = 0; m < len; ++m)
{
v6 = (v6 + 1) % 256;
v27 = *((unsigned __int8*)box + v6);
v25 = (v27 + v25) % 256;
box[v6] = box[v25];
box[v25] = v27;
Src[m] ^= box[(unsigned _int8)(v27 + box[v6])];
}
}
void print(unsigned char* data) {
for (int i = 0; i < 44; i++) {
printf("%c",data[i]);
}
}
unsigned char Src[256];
char out[256] = {-33,-57,77,20,-63,-20,8,-28,95,63,3,-76,-112,74,-71,-113,-113,-6,113,67,-57,-15,-99,-35,79,-64,18,68,92,-99,-120,54,45,22,29,-19,-68,-17,-69,91,-97,119,-21,88 };
char key[] = "easy_GUI";
int main() {
unsigned char box0[256];
unsigned char box[256] = {
0x31, 0x74, 0x54, 0x20, 0x03, 0x53, 0x78, 0x70, 0x3A, 0x35, 0x65, 0x42, 0x04, 0x6B, 0x1F, 0x43,
0x06, 0x37, 0x00, 0x76, 0x21, 0x08, 0x0B, 0x13, 0x52, 0x4B, 0x2F, 0x1A, 0x59, 0x2C, 0x56, 0x51,
0x7F, 0x3B, 0x0E, 0x05, 0x26, 0x15, 0x25, 0x63, 0x64, 0x7A, 0x3C, 0x29, 0x41, 0x2A, 0x12, 0x17,
0x2E, 0x39, 0x57, 0x3D, 0x66, 0x33, 0x44, 0x6C, 0x6F, 0x47, 0x16, 0x71, 0x5F, 0x1C, 0x14, 0x5A,
0x0C, 0x4F, 0x01, 0x30, 0x1B, 0x68, 0x0F, 0x62, 0x3F, 0x18, 0x69, 0x6D, 0x7E, 0x5D, 0x6A, 0x28,
0x22, 0x5B, 0x55, 0x72, 0x09, 0x5E, 0x02, 0x3E, 0x50, 0x7B, 0x46, 0x45, 0x38, 0x10, 0x48, 0x79,
0x60, 0x36, 0x61, 0x6E, 0x2D, 0x49, 0x7C, 0x2B, 0x34, 0x27, 0x11, 0x7D, 0x0D, 0x0A, 0x77, 0x73,
0x58, 0x5C, 0x4C, 0x32, 0x4D, 0x1E, 0x24, 0x40, 0x67, 0x4A, 0x4E, 0x1D, 0x07, 0x75, 0x19, 0x23
};
int len = 44;
for (int i = 0; i < 44; ++i) {
Src[i] = out[i];
}
dec1(key, box0, Src);
dec2(box0);
dec3(box0, Src);
dealboxdec(Src, box, len);
print((unsigned char*)Src);
return 0;
}
|